
Photo by Jaye Haych on Unsplash
General notes about application API keys
Application API keys provide our customers with access to their data in an unsupervised setting, and is specifically intended for use with machine to machine communication. It is recommended to use application API keys rather than user sessions for applications and scripts that require access to our APIs. This makes it possible to avoid sharing your credentials with applications, scripts or unsupervised machines.
The following sections describe in detail how you can create an API key, what kind of rotation scheme we recommend and what our shared responsibility model looks like with regards the security of our customers' API keys.
API key creation
caution
Please always treat each API key as secret and do not share it with any unauthorized persons. An API key allows access to some of your most valuable assets: your data.
In order to create an API key, you need to sign in to our API key management page. Once you have been authenticated, you will be presented with your user detail page which will list all the ships that you have access to in addition to all the permissions which have been granted to your account:
The "API Key Management" section provides a simple interface for creating and invalidating API keys. A list of all your API keys can be accessed there, which will be empty on first visit. A new API key can be generated with the "Add New API Key" button.
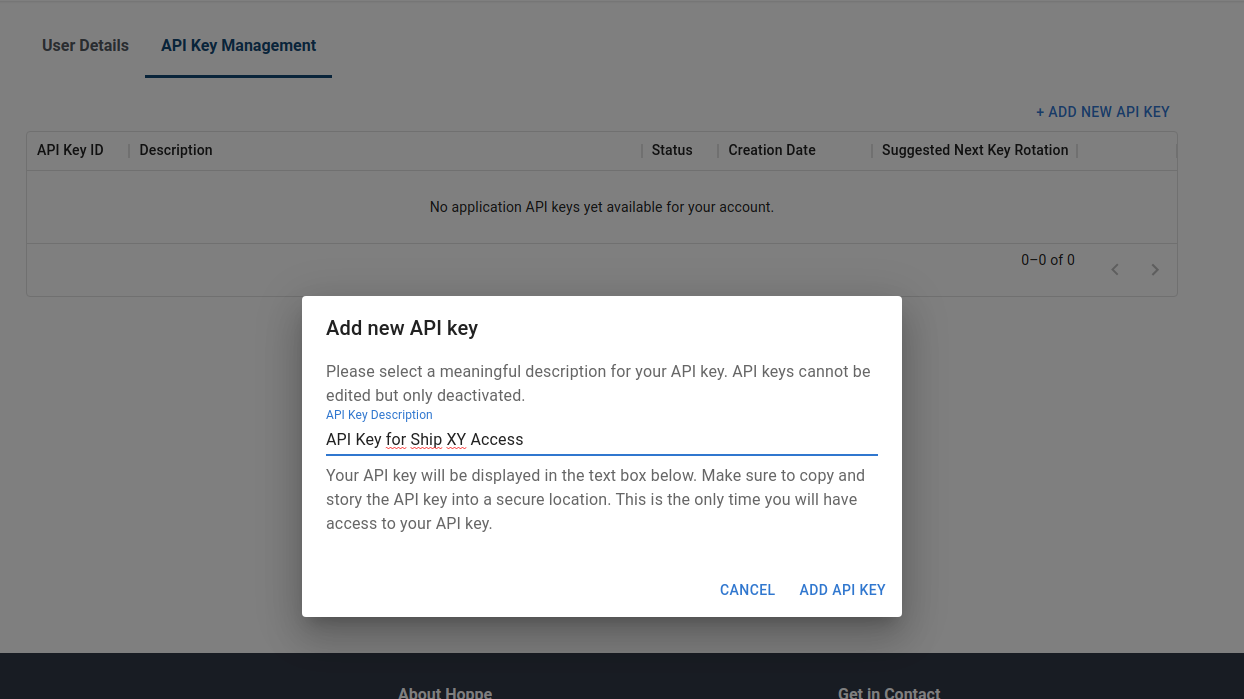
We suggest following the practice of giving your API keys meaningful descriptions in order to easily identify API keys with different purposes later on.
caution
You will only be able to see the API key once, immediately after it has been generated. Once that window has been closed, you will not be able to access the API key's value again. Please make sure to safely store the API key after creation.
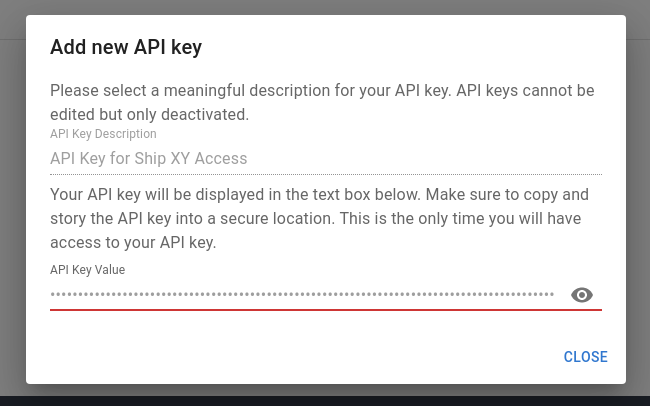
A valid API key must be provided in the Authorization header as Authorization: ApiKey <API KEY VALUE> for each
API request.
API key rotation
We recommend rotating API keys on a regular basis. A once per year rotation is expected to provide decent security with a medium level of effort. API key rotation is simple. Just create a new API key as mentioned above.
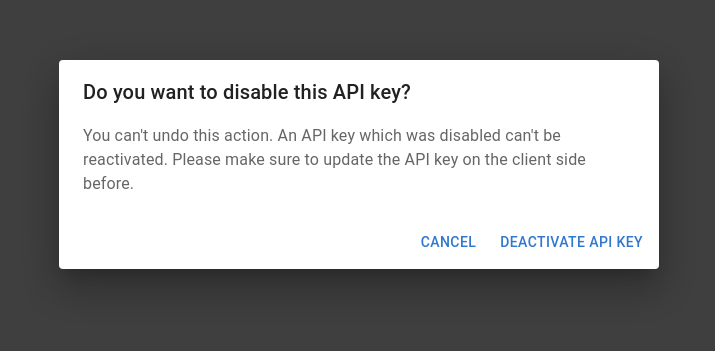
Afterwards, distribute this new API key to your applications and make sure the applications can use the new key successfully. In a next step head to the API key management console and deactivate the old key
API key handling
API keys protect your most valuable asset: your data. Therefore, we highly recommend treating API keys as secrets. Therefore, it is suggested to never share API keys with unauthorized personnel, store them without encryption, send them via email or paste them into untrusted websites.
We highly recommend following the OWASP best practices on API key management.
Shared responsibility model
We do our very best to protect your data at every point in time at the highest level of security. The safety of the API keys, usernames and passwords, however, lay in the full responsibility of our partners and users.
Still, we are keen to assist you in supporting you to come up with secure and safe architectures when it comes to managing secret material or accessing our APIs. Never hesitate to reach out to moc.eniram-eppoh@snoitulosatad.
About the Authors
 Dr. Klaus Hueck is Team Lead of the Data Services team at Hoppe Marine's R&D department. He has been responsible for leading the development of Hoppe's cloud infrastructure and the Ship-to-Shore data transmission technology. With a strong background in software development and physics he enjoys breaking down complex tasks into workable packages to build tailor made solutions focused on our customers needs.
Dr. Klaus Hueck is Team Lead of the Data Services team at Hoppe Marine's R&D department. He has been responsible for leading the development of Hoppe's cloud infrastructure and the Ship-to-Shore data transmission technology. With a strong background in software development and physics he enjoys breaking down complex tasks into workable packages to build tailor made solutions focused on our customers needs.In his free time, he is a passionate sailor and beekeeper.